COMPONENT / IDENTITY OBSERVABILITY
Identity Security in Real Time
Gain immediate clarity on who has access to what, identify over-privileged accounts, and reduce risk in a fraction of the time.
One location for squeaky clean identity hygiene
Identity data is every organization’s greatest attack vector. Our Real-Time Data Lake is the bedrock of the industry’s leading security posture management solution.
Assess security risks in seconds
An intuitive map of your identity system with 360° visibility, an intelligent risk collaboration hub, and seamless AI-powered risk remediation workflows.
Check out off-the-shelf connectors
We feed a Global User Profile to all your identity tools.
Don’t see yours on the list? Just ask.
OUR CUSTOMERS
Hackers hate us. Customers love us.
Identity visibility is critical for highly regulated industries and organizations. Learn how our central intelligence hub solution boosts security and compliance.
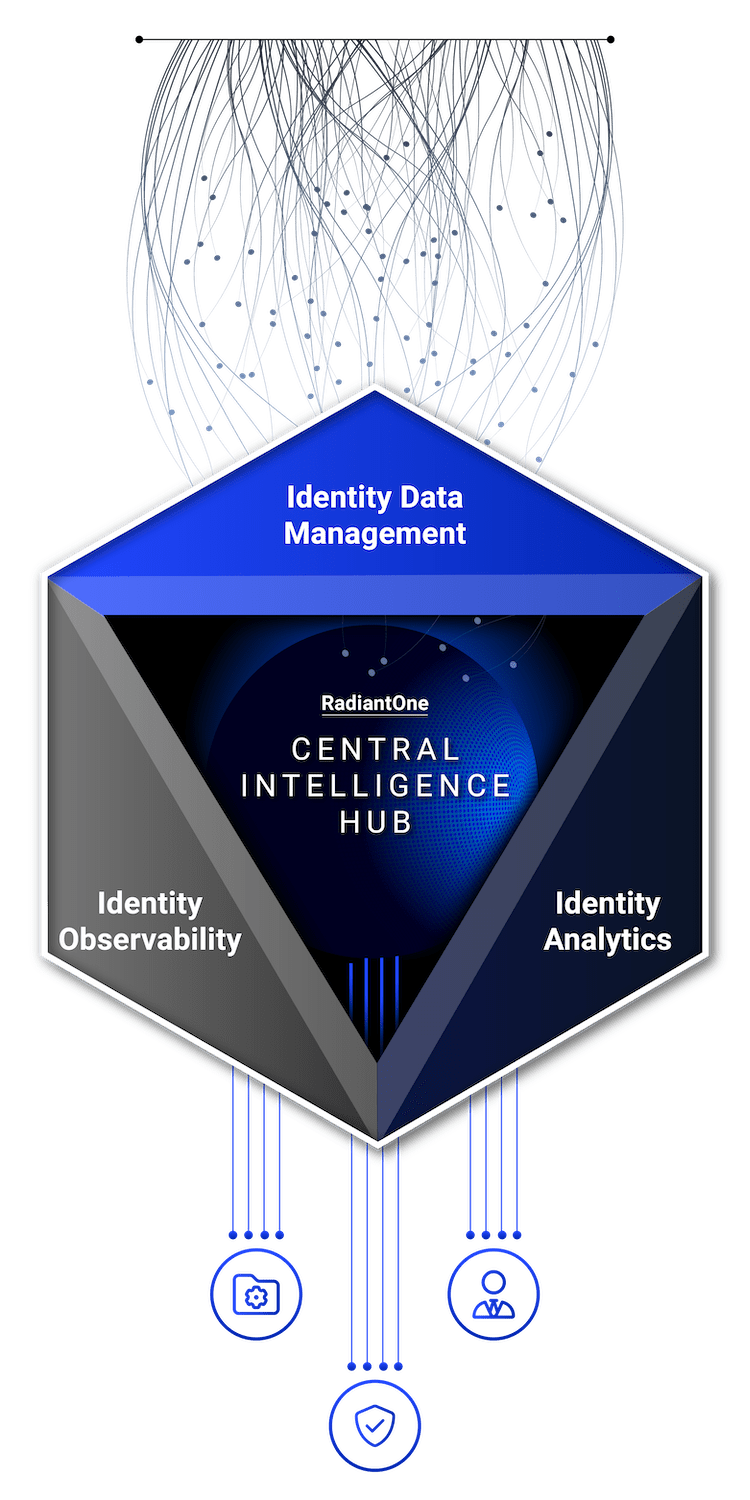
YOUR CENTRAL INTELLIGENCE HUB SOLUTION
Ironclad security starts with clean data & laser sharp analytics
Identity Observability relies on the foundation of Identity Data Management and Identity Analytics. Learn how we deploy these tools synergistically to increase identity health.
Integration
Step one is fully connected identity data. Eliminate silos by unifying all identity sources, providing a single source of truth and consolidated view of all people, machine identities and access privileges.
Synchronization
It doesn’t matter to us whether your data sources are on-prem, in the cloud, or a hybrid of both. Synchronize all Global User Profiles with bi-directional connectors that propagate identity data and keep it coherent across all systems.
360° Visibility
Keep auditors and regulatory bodies happy with automated user access reviews, intuitive risk scoring, and AI-powered analytics that accelerate data cleanup, simplify compliance, and mitigate risk.
It’s time to bulletproof your identity infrastructure
Learn how Radiant Logic improves identity data quality, delivers actionable insights, and strengthens security posture.