Getting Started / Architecture
We invented the virtual directory, but we didn’t stop there
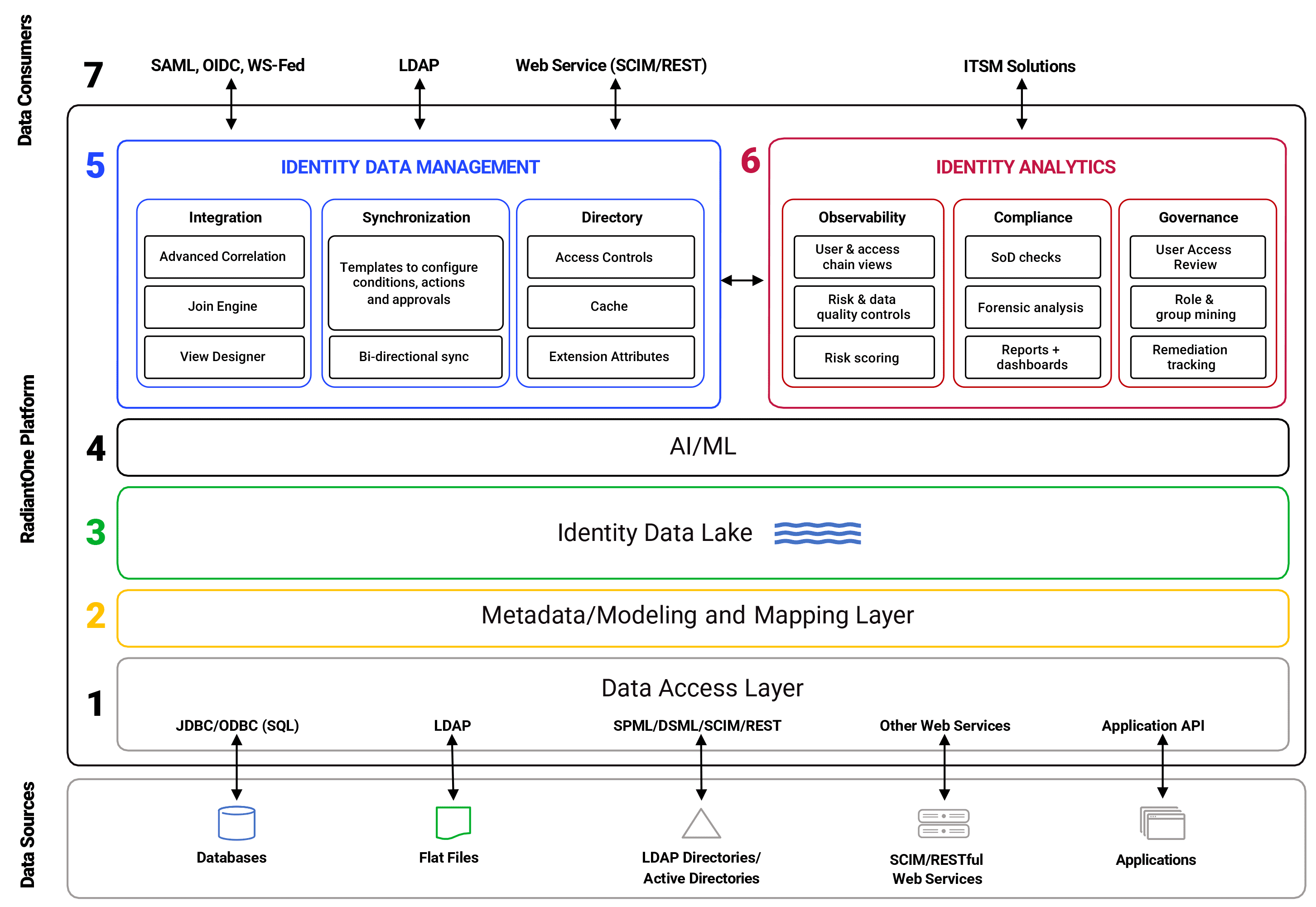
Integrate identity across diverse, dispersed systems and create an authoritative source—then enhance with analytics to supercharge human decision-making.
A flexible identity data layer
Working seamlessly with existing solutions, RadiantOne builds the organization’s definitive identity and context source. With RadiantOne, organizations can leave systems in place, or facilitate easy transitions from legacy technology at their own pace–while speeding initiatives, enhancing security, and making the identity team’s life a little (actually, a lot!) easier.
Not all solutions play nice with each other–RadiantOne helps them interoperate so you can avoid heavy customizations, endless rounds of re-work, and manual processes. Deliver all the data, to all of the consumers, for a fully mature IAM system.
- De-couple the architecture to deliver identity on tap
- Reduce custom integrations–stop copying data
- Don't rely on brittle hard-coding
- Avoid vendor lock-in
- Prevent over-provisioning and over-privilege
Identity Data Management integrates existing identity sources to create a re-usable asset that can meet new requirements, infinitely. Identity Analytics delves into unified identity data to provide visibility, improve data quality, and mitigate risk.
- Build it (a complete source of identity truth) once, re-use it everywhere
- Gain insight into users, entitlements, permissions across the infrastructure
- Implement access best practices faster
- Make changes without disrupting services
- Speed and simplify governance and compliance
RadiantOne Identity Data Platform
We make it look easy: peek under the hood at how we get it done.
What is an identity data platform?
And how is this different from other identity solutions on the market? Radiant Logic has focused on the identity data layer—our approach is all about unifying identity to streamline access and improve identity operations across the array of decision points that exist in the IAM system. These identity consumers all rely on fast access to high-quality identity data: that’s what we bring to the table.
You’ve seen the architecture—now see it in action.