The Rise of the Identity Data Fabric
- Heather MacKenzie
- January 14, 2022
- Identity and Access Management
- 5 MIN READ

Fabrics–so hot right now. Identity Fabric. Data Fabric. Cybersecurity Mesh. In fact, Gartner named data fabric and cybersecurity mesh (which includes the Identity Data Fabric as a key component) as two of its top strategic technology trends for 2022. When you look at the commonalities, the underlying formula is actually pretty simple: [integrate data + connect processes] = [reduce complexity + achieve business goals].
The key takeaway? It’s all about the data–it’s the thread in your fabric–and you need it as a foundational layer in your enterprise IT architecture. In the world of Identity and Access Management, without a comprehensive picture of who has access to what, what each user is allowed to do, and being able to adapt quickly as things change or business needs shift—your whole infrastructure becomes hostage to your identity processes and the quality of your identity data.
Identity, Identity Everywhere
First, let’s look at some of the problems facing today’s enterprises. Thanks to decades of inorganic growth, move to the cloud, piecemeal IT solutions, and more recently, the rapid and unplanned move to remote work, there’s an exponential amount of IT complexity and a proliferation of identity siloes in the enterprise. In fact, a 2021 survey by the Identity Security Alliance reported that 83% of respondents had seen an increase in the number of identities within their organization in the past year. This sprawl leads to tremendous technical debt, turning identity and access management into a roadblock for many organizations, and vastly expanding the attack surface.
If identity sprawl was a problem before, it’s exploded since the pandemic. Well-intentioned remote users signed up for productivity apps–think Dropbox, Slack, Trello–likely outside of the domain of the enterprise IT team. Enter the presence of shadow IT. And this problem will be with us for a while–as of today, only 4% of large enterprises are fully in the cloud.
This identity sprawl has led to overwhelming complexity, and it takes a heavy toll on resources. While organizations want to embrace digital transformation and move to the cloud, they’re weighed down by an immense amount of unreachable identity data. Every new identity project takes much longer than anticipated, demands huge costs in customization, presents a huge burden on staff across the enterprise, and reveals security gaps due to the complexity and inflexibility of the legacy infrastructure. Many projects get stuck and organizations settle for “good enough” instead of wasting more time and resources trying to resolve the problem for good. It’s no wonder that cybersecurity breaches continue to skyrocket.
Identity data silos cost more than just time, money and resources—it inhibits forward progress, causes employee frustration, and creates a poor customer experience. But don’t worry-there IS a better way forward.
Identity Fabrics: A Part of Identity-first Security, but Not Enough
Leading analyst firms are now introducing identity fabrics as a way to organize and manage a distributed identity system. It’s a featured topic at this year’s Gartner IAM summit, and KuppingerCole is now creating a leadership compass for identity fabrics. It’s a modern conceptual approach to security architecture, enabling the distributed enterprise to deploy and extend security at the asset itself.
The piece that they’re missing is that these architectures depend on being able to access quality identity data.
In a recent webinar, analyst Martin Kuppinger describes the identity fabric as a paradigm for architecting a future IAM. He also says, though, that “A main challenge in IAM is dealing with identity data–relationships, integration, and identity information quality.”
You need the data to make these security decisions–without it, your cybersecurity mesh is operating without all the necessary info. It’s like flying a plane without weather data or a working GPS. The engines will run, but you’re lacking critical information to operate in the safest manner.
What if we could introduce a data fabric for the identity world, making unified identity data available everywhere it’s needed, regardless of its original source?
Needed: A Radically Simple Approach
IAM tools would be more effective if they had one consistent place to connect to up-to-date identity data in their desired format, in an instant. One location to access the identity data needed, in the exact protocol needed, delivered on-demand. No complexity or customization needed.
That is the promise made by a new category known as the Identity Data Fabric–it’s an integrated layer of identity data (fabric) that connects to all the different sources of identity, unifies the data into global user profiles, and makes that data accessible in the exact format required by the consuming applications or services. In a nutshell, it automates the painstaking tasks of aggregating, joining, correlating and synchronizing identity data from disparate identity silos into one authoritative identity data feed.
As opposed to the identity fabric, an Identity Data Fabric focuses on unifying the identity data itself, rather than trying to integrate identity at the application layer. Instead of having every identity tool repeating and duplicating the same integration efforts–a common response to identity sprawl–the Identity Data Fabric serves up unified identity data on-demand to each application and service, using the access protocol of choice.
Build it once, reuse it everywhere. It’s the radically simple approach to managing identity in a complex world. And it provides fast, highly-available access to the information needed to fuel modern, identity-first security architectures.
How Does It Work?
The RadiantOne Intelligent Identity Data Platform is the industry’s first Identity Data Fabric. We use patented identity unification technology to:
- Abstract identity data from any and all sources,
- Build enriched global user profiles; and,
- Deliver real-time identity data on-demand to any service or application
Our identity knowledge graph–unique in this space–extracts and represents relationships down to the attribute level, allowing users to stitch together the next generation of zero trust security policies, customer data profiles and machine identities.
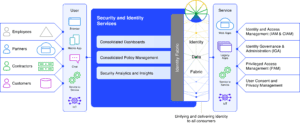
Caption: An Identity Data Fabric serves as a foundation for the rest of the identity infrastructure.
What Problems Does an Identity Data Fabric Solve?
Basically, an Identity Data Fabric turns enterprise identity from an obstacle to an asset.
Through increased visibility, and a unified global profile of each user, it’s much easier to reduce common security risks such as users with excess privileges, or recognize active accounts from former employees. It also allows organizations to easily scale up and accommodate any new elements as the company continues to grow and support digital transformation or IT modernization initiatives.
An Identity Data Fabric:
- Improves Customer Experience: The customer journey involves digital tech, yet this data often sits in disparate silos. An Identity Data Fabric unifies identity data to enable personalized experiences. One major cruise line used RadiantOne to create a holistic view of users that enabled 15% revenue growth.
- Drives Efficiency: Mission-critical applications can take months—or even years—to roll-out, due to chaos and hard-coding in the identity infrastructure. A global hospitality giant modernized their IAM infrastructure with RadiantOne, reducing time-to-market for new projects by at least 6 months by enabling developers to create new dev environments in minutes instead of months.
- Minimizes Risk: A Zero Trust approach relies on attributes to enable progressive disclosure, yet many sizable organizations face identity complexity and fragmentation, making informed security decisions impossible. Radiant Logic was recently selected as an collaborator in NIST’s National Center of Cybersecurity Excellence Implementing a Zero Trust Architecture project.
The Path Forward
Identity will continue to be at the heart of business IT for years to come, as organizations continue to grow rapidly, accommodate the unknowns, and operate in a hybrid model. We need a clear and accessible system to manage identity sprawl. However, addressing identity sprawl at the level of each application and leaving data in isolated silos with minimal visibility can be incredibly risky, with the threats of data theft, malware, and ransomware lurking.
An Identity Data Fabric approach–weaving together identity data and putting it to work in the enterprise–will save vast amounts of resources, money and time further down the road as new threats arise.
Explore more
Subscribe to receive blog updates
Don’t miss the latest conversations and innovations from Radiant Logic, delivered straight to your in-box.