How to Monitor Cybersecurity Threats with Identity Analytics
- Sebastien Faivre
- May 23, 2023
- Cybersecurity
- 8 MIN READ

In our last blog article in this series, we will address the trend of moving tools, systems and applications to the cloud. The necessity of this was accelerated during the recent global pandemic but, surprisingly, remains the norm for many companies since that time. A great percentage of a company’s workforce remains at home, accessing the tools they use on a daily basis in the cloud. Both of these phenomena have exponentially increased the threat of breaches and other malicious cyber-attacks.
The proliferation of the Zero Trust posture within organizations has heightened the awareness of the importance of identity within this framework. The Zero Trust model requires that all users of a company’s systems and resources, whether internal or external, be authenticated and authorized prior to them being given access. The three pillars of Zero Trust are risk awareness, least privileged access and continuous access verification.
Here is an example of the most common risks associated with poor identity and access rights management.
A former Employee Still has Access to Company Resources
While at first glance this may seem unlikely, it is actually much more common than imagined. According to a survey conducted by Brainwave GRC, 90% of former employees retain access to the organization’s applications for more than three months after they have left the company. The departure of an employee or the end of a collaboration with a service provider or partner are part of the daily life in most organizations and can, in some cases, go unnoticed with regard to IT processes and procedures. Two main cases can be observed.
- The affected accounts remain unused
- These are referred to as dormant accounts because they have not been used for a long period of time. Dormant accounts are forgotten and represent a prime target for attackers wishing to break into information systems because they escape the organization’s vigilance
- The affected accounts are still being used
- According to a survey conducted by Brainwave GRC, 43% of accounts that are assigned to departed employees are still being used. This can have a serious impact on the company, as highlighted in the following examples
- If the account is used by the former employee himself or herself, and the employee has left the company in a contentious context, the risk of malicious activity is high and presents a real danger to the company’s assets
- A former employee may have meant well by passing on his or her login and password to a member the team as part of a job handover, but this convenient method of going around the system can have dire consequences with regard to security
- At times, an account remains active in order to maintain a service or an application in operation. However, this means that logins and passwords are shared without any trace of this exchange being recorded in the system. In this case, it is impossible to know exactly who is accessing what, and for what reasons
Whatever the case, an organization is exposed to a multitude of risks where dormant accounts are concerned, risks such as sabotage, data leakage or theft and business disruption.
Access Rights and Mobility: Excessive Privileges and Toxic Combinations
At the beginning of 2022, 74% of organizations that fell victim to cyber-attacks believed that legitimately granted permissions and privileges was one of the main factors that incited the attack.
This figure highlights the notion that privileged access is a prime target for hackers. It is not surprising since these accesses are intended to protect the organization’s critical assets and designed to allow a certain number of sensitive operations to be undertaken. Hacking into them allows the perpetrator to quickly take control of an organization’s information systems, as witnessed by the cyber-attack that Uber faced during 2022, among others. The need to perfectly control the granting of privileged access through the use of a Privileged Access Management (PAM) solution, in particular, is key.
In addition to scrupulous regulation of the use of privileged accounts, the granting of even standard access rights can also lead to abuse and generate cybersecurity risk.
In the context of internal mobility, for example, extreme caution is required regardless of the nature of the access rights the employee has, and this for several reasons:
- The scope of an employee’s mission has evolved. Are the access rights that were necessary for him to perform his former duties still legitimate, or should they be removed?
- Would granting additional access rights linked to his new job function create any risk?
To determine this, old and new access rights must be examined closely. Otherwise, it could be that the employee’s actual access rights exceed the three founding principles of access rights security, which are:
- Least privilege
- Need-to-know, and
- Segregation of Duties (SoD)
In the case of SoD, for example, a person with access rights that allow him or her to modify a bank account number in a payroll application while simultaneously being able to perform a financial transfer accumulates access rights that are incompatible with each other. Moreover, if these access rights are, in fact, of a privileged nature, the employee has full power over the organization’s information systems. The risk of internal fraud is, therefore, present, and the hacking of an account of this type constitutes a golden opportunity for those with malicious intent.
Solutions for Monitoring Cyber Threat: Identity Analytics
Whatever the means deployed, it is highly likely that an organization will one day be forced to deal with a successful attack. By the time it is identified, it may already be too late. In some cases, the intrusion at the origin of the attack will have taken place days, months, or even years ago. In this case, the information systems could already be compromised, and the repercussions considerable. To avoid this, it is recommended to consider software solutions that provide protection, such as RadiantOne Identity Analytics powered by Brainwave GRC.
Identity analytics-enriched solutions such as Identity Analytics, help reduce the attack surface. If poor management of identities and access rights increases this surface, efficient and effective management reduces it and forces the attacker to execute lateral movements to access the organization’s data. Identity analytics can help to take action:
- Preventively, by reducing the attack surface by reducing access rights, and
- Proactively, by uncovering attacks in progress by analyzing behavior and associated drift
This can be done by enabling the collection, correlation and analysis of complex and disparate access data such as accounts, groups, permissions and logs. Using an identity analytics solution enables this by ingesting data of all types in an agnostic manner, followed by the correlation and analysis of this data.
Shedding Light on the Organization’s Identities and Access Rights
By collecting the data associated with access rights, no matter the origin (HR tools, directories, legacy applications, ERP, SaaS, etc.), Identity Analytics provides the ability to correlate identities, accounts and access rights located in the information system. This helps build the chain of access, whether or not they are managed by an Identity and Access Management (IAM) tool. Data quality issues can be uncovered and corrected, and a 360° view will show who can access what, when and why.
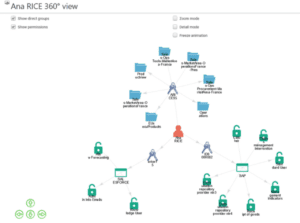
Automate Access-Related IT Checks with Prescriptive Analytics
Once the access chain is built, simplify the execution of access rights controls and automate access reviews. Increase their frequency in order to move from a posture of compliance to one of risk mitigation.
- Save Time
- Once configured, Identity Analytics automates everything to provide a continuous, risk-based view of the situation. In this way, inquiries by managers, auditors and other stakeholders can be answered quickly and easily.
- Make Controls More Reliable
- As mentioned above, human error is common and is considered to be a vector for risk. By using Identity Analytics with IT and SoD control engines, the margin of error attributable to teams is greatly reduced.
- Optimize Costs
- By providing teams with clear, documented data sets and automating everything possible, access controls are worth the cost.
- Motivate and Encourage the Team
- Reviewing access rights is often perceived as a time-consuming, tedious, and burdensome exercise. In order to meet deadlines, it is not uncommon to find that the access rights being reviewed have been validated quickly and without taking a long, hard look at the data itself. Providing user-friendly interfaces that can be understood by all stakeholders in the access review process avoids this type of situation because teams are more likely to focus on the key areas of concern in order to make informed, relevant decisions.
- Instill a Spirit of Collaboration
- Automating access-related controls and reviews allows different teams to work together more efficiently, down to the company’s first line of defense, keeping the organization’s assets protected and secured.
Additionally, mash-up dashboards and reports that solutions such as Identity Analytics provide are excellent tools for analyzing and controlling the risk related to access rights and help to avoid unusual and atypical situations. Risk factors associated with an identity or access right can be identified and the correct remediation undertaken, including revoking access rights, increasing the frequency of controls, and modifying a role that was assigned to a given identity.
Using Identity Analytics contributes to the control and reduction of risk associated with identities and access rights and offers a decision support tool to manage any cybersecurity strategy more easily by focusing on the situations that generate the most critical risk.
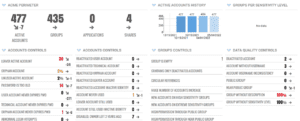
By covering the perimeter of identities and access rights present within an organization, Identity Analytics not only provides an exhaustive visibility of the scope of each granted access right, but it also allows for the detection of abnormal behaviors and deviations using machine learning and risk-scoring analytics. It is imperative to continuously assess IT systems to uncover anomalies and mitigate the associated risk before it is too late.
In Conclusion: Cybersecurity risk linked to Access Rights is Everyone’s Concern
As cyber threats and ransomware attacks continue to proliferate, organizations must take more and more precautions to counter these potential attacks. At the same time, a paradigm shift is taking place. In the age of multi-cloud and big data, traditional cybersecurity models that set up the enterprise as a fortress are collapsing in favor of adopting a Zero Trust posture, thus eliminating the notion of implicit trust.
Identity, login and password theft have become commonplace, and the internal threat is real. Therefore, protecting identities and access rights must be at the heart of an organization’s concerns. Securing them in an optimal way is crucial to preserving the integrity of its assets. To achieve this, the steps to follow are summarized here. They must be able to:
- Question existing cybersecurity strategies applied to identities and access rights to adjust them to both the evolution of threats and the complex architecture of their hybrid infrastructures
- Adopt an approach that allows them to identify and control identity and access rights risks
- Implement a solution that enables them to industrialize the execution of identity and access rights controls
- Use analytics tools in a preventative manner to identify any unusual situation that could potentially pose a risk
With the integrity of an organization’s assets at stake, securing identities and access rights is the only way to face cyber threats head on.
We hope this blog series was informative and helped enlighten you about the best mode of prevention: monitoring access rights by using an effective and efficient identity analytics solution.
Be sure to join us at the upcoming Identiverse conference from May 30 through June 2 in Las Vegas, Nevada, and speak to our experts who can get you started on the way to solidifying your company’s cybersecurity strategy.
Explore more
Subscribe to receive blog updates
Don’t miss the latest conversations and innovations from Radiant Logic, delivered straight to your in-box.